Wearable Biometric Authentication That Stops Phishing & Ransomware
Get FIDO2-compliant, next-gen MFA with biometric and proximity-based login — stops phishing and social engineering attacks where legacy MFA fails.
A Next-Generation MFA wearable that takes user vulnerabilities out of the security equation to defeat the most sophisticated attacks
Phishing makes your users the weakest security link
With more than 90% of successful cyberattacks starting with a phishing email (source: CISA 2024), it’s time to take employees out of the security equation. All it takes is a single user falling prey to a well-engineered phishing attack to expose the entire business to a breach event with costly regulatory, financial and brand impacts.
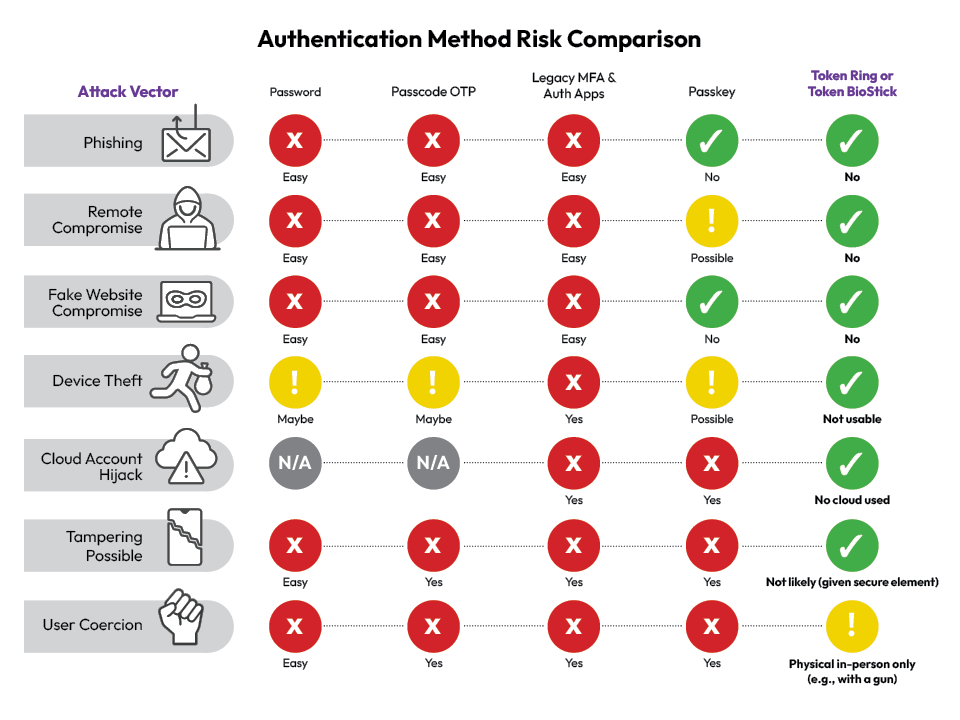
Token Ring effectively mitigates user vulnerabilities
Token Ring offers next-generation multifactor authentication with phishing-resistant, FIDO2 compliant technology, that eliminates the reliance on legacy MFA OTPs, passwords, and employees to reliably spot every phishing email, which is impossible. This wearable integrates cutting-edge, biometric authentication technology in a compact, comfortable, and user-friendly design.
Watch How Fast You Can Login into Windows with Token Ring
Why Token Ring?
Secure Communication
The versatility to authenticate via fully secure NFC or BLE technologies mitigates even the most complex attacks.
Passwordless Authentication
The gesture feature allows the user to authenticate only when they intend to.
Upgradeable Firmware
A future-proof design ensures the Ring can be optimized for performance and new capabilities in a flash.
Biometric Authentication
The FIDO2-compliant capacitive fingerprint sensor in Token Ring ensures only the user’s fingerprint will activate it, meaning no one else can.
.png?width=250&height=346&name=TR3-Upright-Left-Angle-large%20(2).png)
Innovative Wearable
The ring is always with the user, so it is always safe and immediately available.
Secure Credentials
User credentials are stored on Token Ring EAL5+ certified secure element for high security.
Fully Interoperable
The Ring is fully compatible and can be deployed seamlessly with all leading IAM platforms within hours.
Proximity-Based Login
The ring ensures authentication only occurs when it is near the intended device, preventing man-in-the-middle attacks and enhancing security.
Award Winning Cyber Security




Setup Your Biometric Authentication With Ease
Token Ring Works In 3 Easy Steps
Download App and Connect Your Ring
Charge Your Ring and Pair
Scan Your Fingerprint
Wear the Token Ring and scan the tip of your finger. Once you have scanned your fingerprint your Token Ring it is ready for use!











See what next generation MFA can do for your organization.
Deliver the greatest user convenience and the strongest security with wearable biometric ring authenticators
FAQs
1) Mobile phones are vulnerable to SIM Swapping where the attackers trick the phone company into transferring the mobile number to a new SIM card, then the attacked receives all SMS messages, including OTPs.
2) SMS is not encrypted end-to-end, which means that messages can be read by cybercriminals while they are in transit.
3) Mobile phones get lost and stolen, then attackers have direct access to SMS messages and authentication apps on the stolen device.
4) SMS messages can be intercepted in various ways, such as when over un-encrypted or insecure networks allow attackers to read messages.
5) Many users inadvertently download malware onto their phone that intercepts SMS messages and forwards them to cybercriminals.
FIDO (Fast Identity Online) passwordless solutions offer many security benefits by eliminating the use of traditional passwords. This includes:
1) Eliminates Password Vulnerabilities
2) Resistant to Common Attacks
3) Uses Strong Cryptographic Authentication
4) Local Device-Based Authentication
5) Enhances User Convenience and Security Compliance
6) Prevents Account Recovery Exploits
By leveraging FIDO’s passwordless approach, organizations can significantly reduce the risk of security breaches, improve user experience, and comply with evolving security and privacy regulations.
1) They frequently get lost.
2) They often get left plugged into computers. Leaving a dongle plugged into a device is like leaving your keys in your car when you are away from it.
3) They only plug into USB ports [no Bluetooth or NFC support]. Token ring works via NFC and BLE so it can be used with any device
4) They are often not with the user when they need it wherever they are working and with whatever device they are using.